How to enable and configure CSP for Magento 2
:quality(80))
With Magento v.2.3.5 a new feature was introduced called CSP (Content Security Policies). This is a tool to increase security for Magento applications and protect against Cross-Site Scripting (XSS) and related attacks, including card skimmers, session hijacking, clickjacking, and more.
By default, CSP is set to ‘report-only’ mode - meaning it will report policy violations but will not respond.
In this article we will explain how to successfully configure CSP to ‘restrict mode’, which means that any violations can be reported and acted upon by the application.
Step 1
Build a new custom module Vendor_Csp with the following file structure:
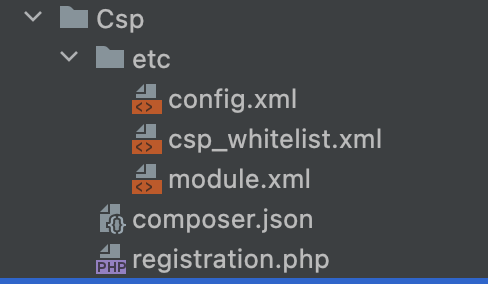
Step 2
config.xml should contain the following settings to ensure that malicious scripts are blocked and not just reported (secure option):
Step 3
In csp_whitelist.xml add the following structure:
Step 4
Next, navigate to the front end of the website on Chrome, right-click anywhere on the page and select ‘Inspect’. This will open the developer tools - in the top tabs select ‘Console’ - here you can see any warnings, errors and other messages related to the page.
Once in the console, add a filter for ‘Refused’, which will make sure that only CSP violations are shown.
Navigate every possible combination of pages on the site looking for any violations and investigate each of them.
Chrome will give details about what type of violation is being blocked. The error message will contain one of the policies listed above.
As an example the following error:
gtm.js?id=GTM-XXXXXX:50 Refused to load the script 'https://www.googleadservices.com/pagead/conversion_async.js' because it violates the following Content Security Policy directive: "script-src assets.adobedtm.com.
This means that https://www.googleadservices.com/pagead/conversion_async.js violates policy script-src
There are two ways to whitelist a domain:
Wildcard
*.domain.com will whitelist every script coming from domain.com. This is handy for examples with clarity.ms where scripts can come from www.clarity.ms` or j.clarity.ms.
While this is the easiest way to whitelist something, it’s less secure due to its lack of specificity. If one sub-domain of the wildcard domain is compromised then we have no protection. It should only be used for well-known, established domains.
By domain
www.googleadservices.com means that everything coming from the www from the googleadservices domain will be allowed.
N.B. https://www.googleadservices.com and https://googleadservices.com are treated differently.
Add a whitelist rule in the form of a value tag within the relevant policy in csp_whitelist.xml:
At the moment, the CSP whitelist is only applied by running bin/magento setup:upgrade so it can be time-consuming.
We advise you set in config.xml, navigate the site whitelisting as many violations as possible and then switch to 0 before testing the whole site and looking for missing rules.
Please note that larger vendors needing scripts added within their modules often already have CSP whitelist implemented. For example, see:
vendor/paypal/module-braintree-core/etc/csp_whitelist.xml